
Kevin Mitnick, “The World’s Most Wanted Hacker” and KnowBe4’s Chief Hacking Officer, gives you the information you need to protect yourself against the strategies and techniques hackers use to take control away from you and your organization.
Digital Attacks
- Phishing: Email-based social engineering targeting an organization.
- Spear Phishing: Email-based social engineering targeting a specific person or role.
- Stop, look, and think before you click that link or open that attachment.
In-Person Attacks
- USB Attacks: An attack that uses a thumb drive to install malware on your computer.
- Tailgating: When a hacker bypasses physical access controls by following an authorized person inside.
- Stop, look, and think before plugging any external media into your computer or allowing someone in that you don’t recognize.
Phone Attacks
- Smishing: Text-based social engineering.
- Vishing: Over-the-phone-based social engineering.
Stop, look, and think before you surrender confidential information or take action on an urgent request.
Social Engineering
Social engineering is the art of manipulating, influencing, or deceiving you into taking some action that isn’t in your own best interest or in the best interest of your organization.
The goal of social engineers is to obtain your trust, then exploit that relationship to coax you into either divulging sensitive information about yourself or your organization or giving them access to your network.
Red Flags
Red flags are a sign of danger or a problem. They can be as subtle as an uneasy feeling or as obvious as an email about “suspicious charges” from a bank that you don’t even have an account with.
Since phishing is the most common form of social engineering, let’s take a closer look at seven areas in an email and their corresponding.
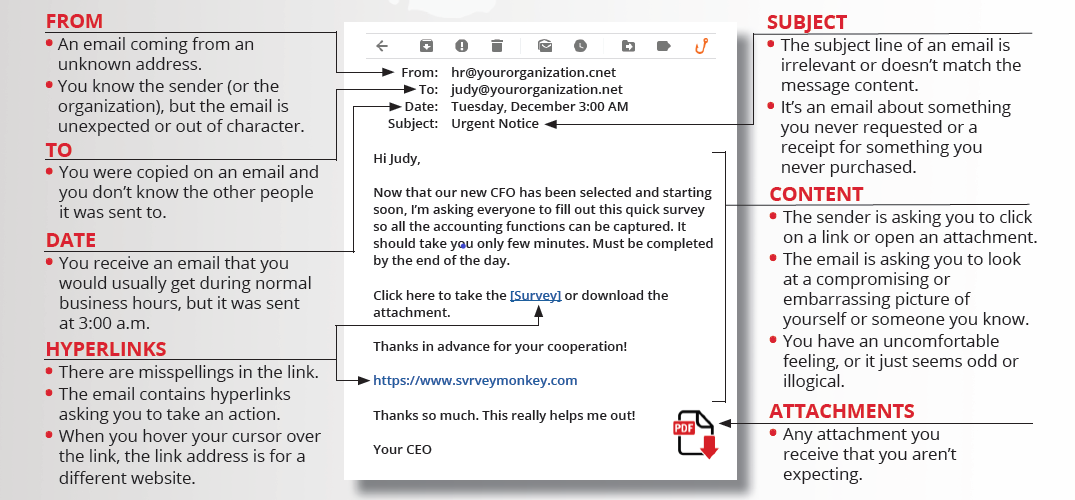
This article is used with permission from our partner KnowBe4.
